

by Dichotomy and the Pros V Joes Crew:
Gold Team:
captain-opsec
Veloce Vettura
Gabe
quicksand
Uplink
matir
idigitalflame
Huzar
Myssfit
ZeroBitSmith
OldSchoolNoise
Blue Pros:
imp0ster
malwaremama
dmfr
techtonic
Rujo
Lazzarus
Buzzsaw
NeedsAMulligan
Spike Roche
Dook
Phantasm
Watchdog
Red Cell:
t1v0
Promina
ifounditthisway
anarkyx
niden
Brimstone
3ndG4me
webyeti
cicadamikoto
0xn00b
Pathetiq
74rkus
faultline
Children of Init
cale
huffy
benny
jon
DetlaCharlie
Mostly Harmless
toomanybananas
Gray Pros:
mark_tangent
Guy Edri
Malloc
Green Pros:
0xdecae
Overclock
On Sabatical
Follow our official Twitter accounts! PvJ Gold Team PvJ Blue Team PvJ Red Team
| Event | When | Pro reg | Joe Reg | Gray Reg |
|---|---|---|---|---|
| BSidesDE | Nov 14 - 15 | Open | Open | N/A |
Our events are an opportunity for average users (Joes) to try their hand at the offensive and defensive side of computer security. For the Pro's, it's a chance to hone and show off their skills, while also helping others to learn and better themselves. Joes are split up into teams, each with two Pro captains, and given their own network to defend against the Pros in our Red Cell. Each Blue network is full of servers and desktops running Windows, Linux, your standard services like DNS, Web, Mail, and a few surprises. The second half of each game takes the Blues to Purple, giving them the chance to break into the other teams' systems for fame and glory. Players need only a laptop to connect to the environment with. Laptops are not in the line of fire.

Pros V Joes events are all supported by CTF Factory, Inc - a charitable, non-profit 501(c)(3) corporation that was founded and is still run by the Pros v Joes Staff. Our core mission is support of the community, providing education and hands-on training to all, for free, in venues such as the BSides community and beyond.
If you're interested in donating and helping us to continue helping individuals grow in their talents and careers, please feel free to donate to our charity.
You can also support us through Amazon Smile! Making your purchase using our Smile link means that Amazon will contribute to our charity on your behalf (it costs you nothing).
Pros V Joes has received assistance from the following sponsors, whom we thank for their contributions.
What's PVJ CTF like? Find out from our players from over the years!
Video preparation from a first time player and then the aftermath following BSDC 2018!
Some tales from HackWest 2018!
A detailed perspective from a first time player from BSLV 2017.
A few Reports from the BSDE 2016 games
An account of the BSLV 2016 CTF
More stories from the BSLV 2016 CTF
Yet another write up for the BSLV 2016 CTF
A concise overview of the game from BSLV 2015.
Another fantastic story from BSLV 2015.
A Blue Team Player's Guide
An enthusiastic report from yet another Joe
One Red Cell member's experience...
What a Rapid7 employee's thought of playing on the Red Cell
The clock is ticking. You glance at the scoreboard and the service is still down. Why didn't that last change fix it? Suddenly a beacon alert pops up under your team name. Shit. Red Cell just took another device. You call out to the captain to let him know that you've lost another host. Frantically, you check the servers you were put in charge of, looking for some sign of pwnage. Netstat, process list...they're all clear. Oh, wait...what's that file in the web root directory? Better kill it just to be sure.
That's better, the beacon went away. But the service is still down, and the other team is ahead of you. Maybe by tweaking this config file here...that did it. It's green again. At least that stopped some of the bleeding.
Then someone taps you on the shoulder and asks if you could help them with their report, they just need to look at a spreadsheet that's on your fileserver. Who is this person? Were they on your team? You can't quite remember. You want to ask the captain, but he's busy with a couple of other team members, chasing out the other two beacons.
You're about to answer the stranger when suddenly your mail client dings. Another ticket has been opened by the scoring engine. Crap, we need to get some funky web app installed in the next thirty minutes or lose 1000 points. This guy is still asking for the spreadsheet, maybe it'd be okay to just let him have a peak so you can get that install done...
Shit, did another pwnage beacon just light up on the scoreboard?
Well, at least we've pulled ahead of the other team...for now...
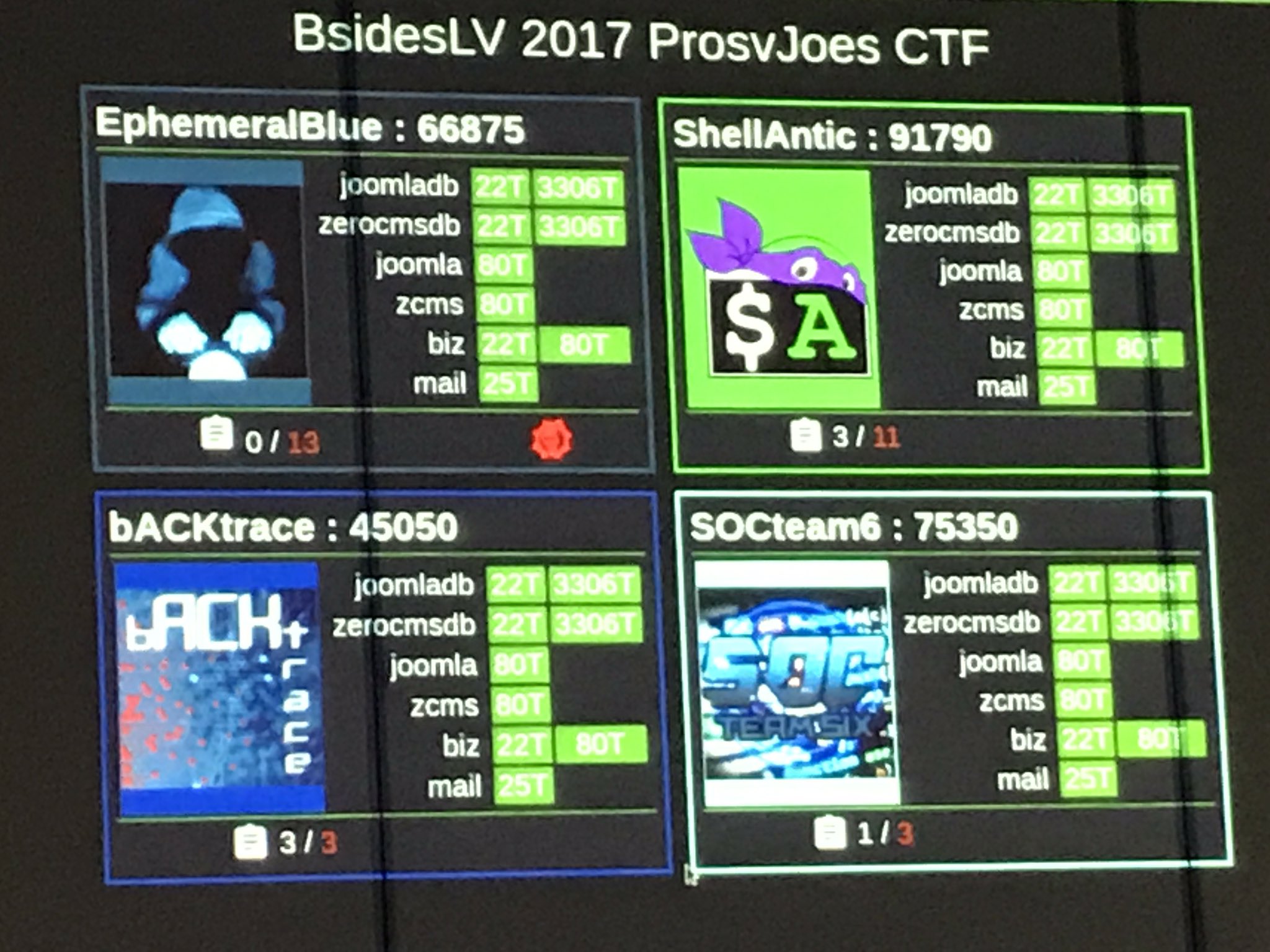
The Pros V Joes's Scorebot software is the heart of the ProsVJoes CTF and has recently undergone a complete rewrite. Designed from the ground up for the unique offense/defense style of play, it has grown along with the game and has become even better than ever with all of the new changes.
It's capabilities include (obviously) scoring the game, monitoring scored services for uptime, tracking flags and submissions, receiving beacons from assets compromised by Red Cell, and interacing with a ticketing system that the Blue Teams receive tasks from. As of BSidesLV 2017, the game now also features the economics portion, where Blue TEams can spend their points on advntages and assets that will help them win the game! Even Red Cell can get into the action!
An open source project, we welcome pull requests with contributions.
The planning for PVJCTF at BSLV2019 is in the final stages. We're focusing on building something new and cool while stabilizing our environment and increasing capacity while fine tuning the additions we made this year.
...but more on that later. ;)
Pros V Joes is the result of literally thousands of hours by over a few dozen individuals to build a realistic environment for players to attack and defend.
This is the admin team, the guys and gals that design, implement, and run the games. We've grown considerably over the years, and have just picked up a few new folks who will be listed here soon...
 Dichotomy
Dichotomy  - founded the CTF and runs the show, but is fortunate and lucky to have such a fantastic team of hackers and geeks on staff, without whom none of this would be possible.
- founded the CTF and runs the show, but is fortunate and lucky to have such a fantastic team of hackers and geeks on staff, without whom none of this would be possible.
 captain-opsec - The Chief of Staff, second only to Dichotomy. One of the key members of the Gold Team Executive Council. He makes sure things get done and keeps it all on the rails.
captain-opsec - The Chief of Staff, second only to Dichotomy. One of the key members of the Gold Team Executive Council. He makes sure things get done and keeps it all on the rails.
 - Former Blue teamer who learned to build, then to break, then to own, then to build stronger, then to break. Now Dev Team Lead and Gold Team key contributor.
- Former Blue teamer who learned to build, then to break, then to own, then to build stronger, then to break. Now Dev Team Lead and Gold Team key contributor.
 Uplink
Uplink  - I need to know what happened at Roswell. Contact me @uplink_snafu
- I need to know what happened at Roswell. Contact me @uplink_snafu
 - an all-out geek that eats CTF for breakfast...
- an all-out geek that eats CTF for breakfast...
 iDigitalFlame
iDigitalFlame  - a major part of the Scorebot dev team, a co-contributor to its core component, the SBE.
- a major part of the Scorebot dev team, a co-contributor to its core component, the SBE.
 Huzar - a long-time staffer with great skills and even greater potential. He's helped build and run many a game, improving what we do at every step.
Huzar - a long-time staffer with great skills and even greater potential. He's helped build and run many a game, improving what we do at every step.
 ZeroBitSmith - been doing security work for ~6 years, mostly focused on incident response and detection infrastructure. He's new to doing PvJ, but had a fantastic time, and is really looking forward to helping make it a great experience for everyone in there future! Super excited to join the team!
ZeroBitSmith - been doing security work for ~6 years, mostly focused on incident response and detection infrastructure. He's new to doing PvJ, but had a fantastic time, and is really looking forward to helping make it a great experience for everyone in there future! Super excited to join the team!
 OldSchoolNoise - a long time veteren of the IT business, recently transitioning with gusto to the security side of things. A great head for hardware and systems administration, this fine gent brings a great deal to the PvJ Family.
OldSchoolNoise - a long time veteren of the IT business, recently transitioning with gusto to the security side of things. A great head for hardware and systems administration, this fine gent brings a great deal to the PvJ Family.
Our staff members on Blue Team are here to help. These Pros will get you trained and ready for the combat to begin on game day, then lead you and support you through the fire once the packets start flying...
 - Long time Linux nerd turned Blue Team Pro/Red Team Hobbyist. Likes whiskey. Prefers sleep to breakfast.
- Long time Linux nerd turned Blue Team Pro/Red Team Hobbyist. Likes whiskey. Prefers sleep to breakfast.
 - Better at asking for forgiveness than permission. Breaks things just for fun.
- Better at asking for forgiveness than permission. Breaks things just for fun.
 - Security engineer. Eats souls for breakfast.
- Security engineer. Eats souls for breakfast.
Pros V Joes has a standing Redcell of awesome, full-time, professional pen testers!
 t1v0 - a dedicated hacker, security researcher and avid CTF gamer. t1v0 has been playing on the Pros V Joes red cell for the several years and looks forwards to pwning blue cell for many years to come...
t1v0 - a dedicated hacker, security researcher and avid CTF gamer. t1v0 has been playing on the Pros V Joes red cell for the several years and looks forwards to pwning blue cell for many years to come...
 Promina - 2o year DoD vet, Instructor, Cyber Patriot Mentor, CTF gamer & Red Teamer. Always looking for a challenge!
Promina - 2o year DoD vet, Instructor, Cyber Patriot Mentor, CTF gamer & Red Teamer. Always looking for a challenge! - software developer and security researcher, and I eat the despair of orphans and lost pets for breakfast.
- software developer and security researcher, and I eat the despair of orphans and lost pets for breakfast.
 Anarkyx - Infosec junkie trying to learn more.
Anarkyx - Infosec junkie trying to learn more. niden - Medic turned hacker, loves breaking stuff and learning how to fix it.
niden - Medic turned hacker, loves breaking stuff and learning how to fix it.
 Brimstone - Participating in Prosvjoes since 2017, brimstone enjoys CTFs year round, whether hosting at local DEFCON and 2600 meetings, or solving them alone or with friends.
Brimstone - Participating in Prosvjoes since 2017, brimstone enjoys CTFs year round, whether hosting at local DEFCON and 2600 meetings, or solving them alone or with friends.
 Faultline - Five years of OffSec has only taught him that there is much more to learn. Always looking for the next stealthy backdoor.
Faultline - Five years of OffSec has only taught him that there is much more to learn. Always looking for the next stealthy backdoor.
 Children Of Init - The more I learn about computers and security, the more I realize I don't know much about computers and security
Children Of Init - The more I learn about computers and security, the more I realize I don't know much about computers and security
 Cale - pop shells not alert()
Cale - pop shells not alert()  Huffy - IT Security specialist with over 6+ years’ experience. Enthusiastic penetration tester with a wide range of talents, built skills based on the principle that offensive security is the most effective security
Huffy - IT Security specialist with over 6+ years’ experience. Enthusiastic penetration tester with a wide range of talents, built skills based on the principle that offensive security is the most effective security
 Benny - Security Researcher and Engineer who loves shells
Benny - Security Researcher and Engineer who loves shells
 DeltaCharlie - Fluent in shenanigans and a pro at breaking things, plays with computers sometimes.
DeltaCharlie - Fluent in shenanigans and a pro at breaking things, plays with computers sometimes. webyeti - Jack of all trades, master of some. Usually found hunched over a glowing screen in the dark or stomping through the wilderness. This is the mystery of the webyeti
webyeti - Jack of all trades, master of some. Usually found hunched over a glowing screen in the dark or stomping through the wilderness. This is the mystery of the webyeti PathetiQ - Appsec pentester and hacker since mid '90s. Trying to get into fuzzing he's also into Purple Teaming.
PathetiQ - Appsec pentester and hacker since mid '90s. Trying to get into fuzzing he's also into Purple Teaming.  Mostly Harmless - Spent about 10 years as a sysadmin and moved into security and pentesting. Participated in several private and government exercises as a red team member.
Mostly Harmless - Spent about 10 years as a sysadmin and moved into security and pentesting. Participated in several private and government exercises as a red team member. toomanybananas - Malware sommelier looking to expand his cellar
toomanybananas - Malware sommelier looking to expand his cellar
In 2016 we've started a permanent crew of Gray Team Pros to help the volunteers at future games. Thanks to Mark and Guy for stepping up!
 Guy Edri - Digital Forensics investigator, H@cker, Reverse Engineering and whiskey junkie. If you got hacked, I AM your DFiR GUY with 25 years experience
Guy Edri - Digital Forensics investigator, H@cker, Reverse Engineering and whiskey junkie. If you got hacked, I AM your DFiR GUY with 25 years experience Malloc - Software Engineer turned Hacker, currently wearing the hat of Security Consultant. Enjoys breaking things, and occasionally putting them back together (with a few modifications).
Malloc - Software Engineer turned Hacker, currently wearing the hat of Security Consultant. Enjoys breaking things, and occasionally putting them back together (with a few modifications).
We've just started a new color, Green! These Staff members will be responsbile for our Associates, the probationary members who show promise but need further opportunity to grow into the role and prove themselves as ready for Staff membership.
 0xdecae - Friendly neighborhood mushroom just looking to turn spores into shells
0xdecae - Friendly neighborhood mushroom just looking to turn spores into shells
 Overclock - Current college infosec student learning to learn as much as I can, have fun learning, and share all I learn.
Overclock - Current college infosec student learning to learn as much as I can, have fun learning, and share all I learn.
Pros V Joes Staff members who have had to step away from our efforts for over a year. We thank them for their contributions and hope they can find the time to return to us very soon!
 Starling - A veteran defender who likes to break things in interesting ways, he brings 20 years of defense-in-depth experience to the playing field.
Starling - A veteran defender who likes to break things in interesting ways, he brings 20 years of defense-in-depth experience to the playing field.
 Wishper
Wishper  - SysAd backgrounds, recovering DBA, tinfoil hats with waxed-paper liner for extra protection. Pulling together diverse teams is part of the fun. Eats bacon for breakfast.
- SysAd backgrounds, recovering DBA, tinfoil hats with waxed-paper liner for extra protection. Pulling together diverse teams is part of the fun. Eats bacon for breakfast.
 Gi0cann
Gi0cann  - has been with us since the start, and has put in countless hours to build and maintain the infrastructure. He is a long time contributor to the scoring engine we use, and is very skilled and upcoming hacker and infosec pro.
- has been with us since the start, and has put in countless hours to build and maintain the infrastructure. He is a long time contributor to the scoring engine we use, and is very skilled and upcoming hacker and infosec pro.
 gambite
gambite  - hacker at heart. Always building or breaking software and a co-contributor to the SBE.
- hacker at heart. Always building or breaking software and a co-contributor to the SBE.
 Rauchoy
Rauchoy  - a key member of PvJ for many years, she's helped us in many important ways, including laying the groundwork for our CTF automation software (not yet released). She's an excellent security practitioner and someone we are lucky to have on staff.
- a key member of PvJ for many years, she's helped us in many important ways, including laying the groundwork for our CTF automation software (not yet released). She's an excellent security practitioner and someone we are lucky to have on staff.
 Dr. Marvin Candle
Dr. Marvin Candle  - freshmen and security analyst for the ███. kernel panic is a constant but I'm here to learn... and to steal memes.
- freshmen and security analyst for the ███. kernel panic is a constant but I'm here to learn... and to steal memes.
Over the years, there have been a number of outstanding people who have donated their time, effort, blood, sweat, and tears to help build this CTF and make it what it is today, as well as what it will be tomorrow.
We'd like to give a shout out to PhobosJ, h4zm4t, and Sail0rl00n for their fantastic contributions
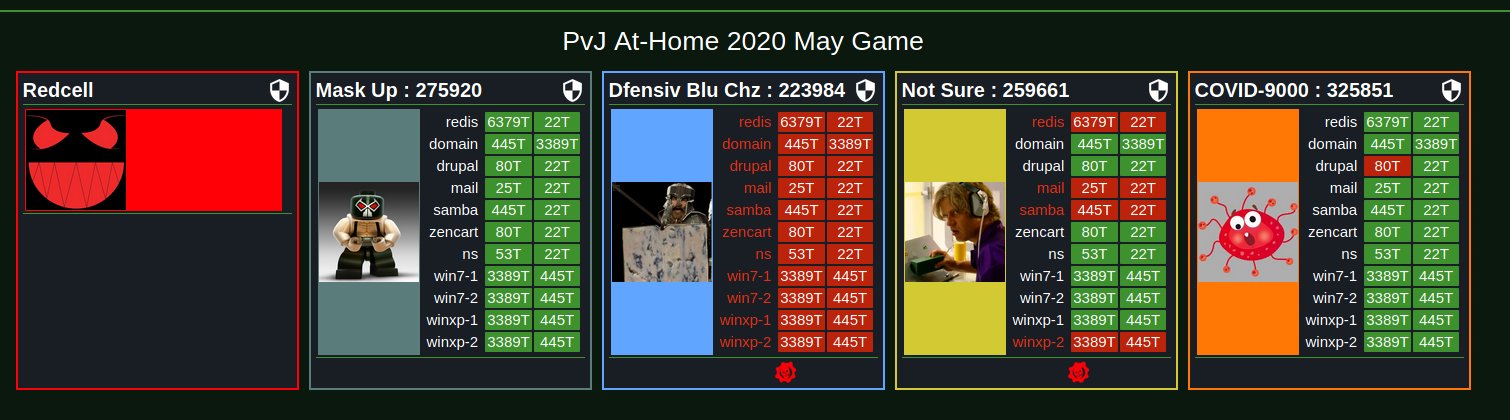
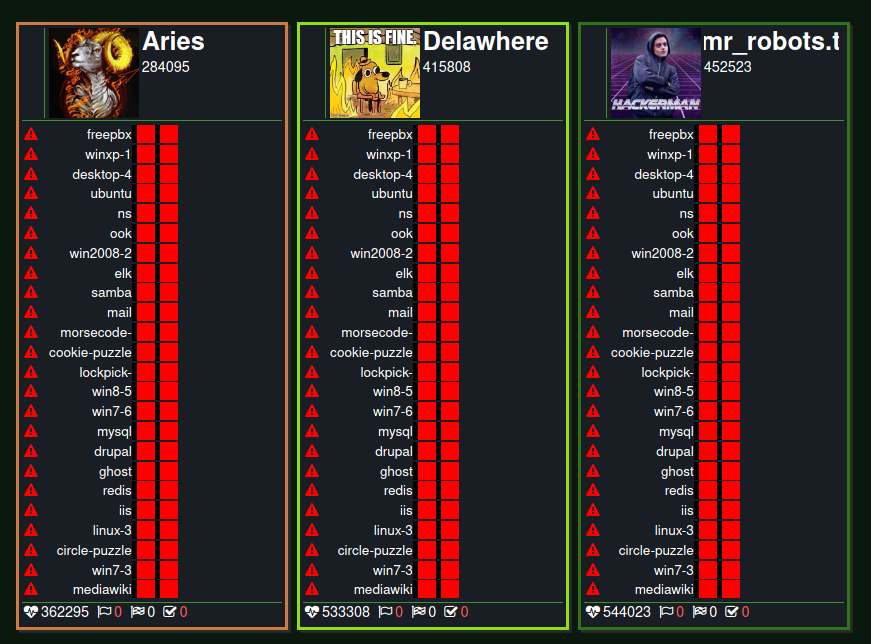
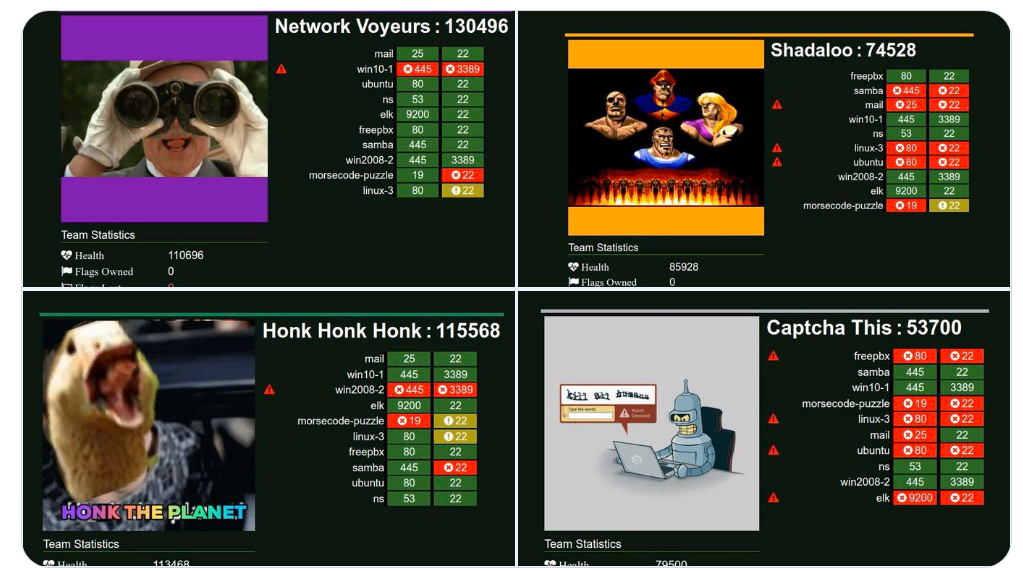
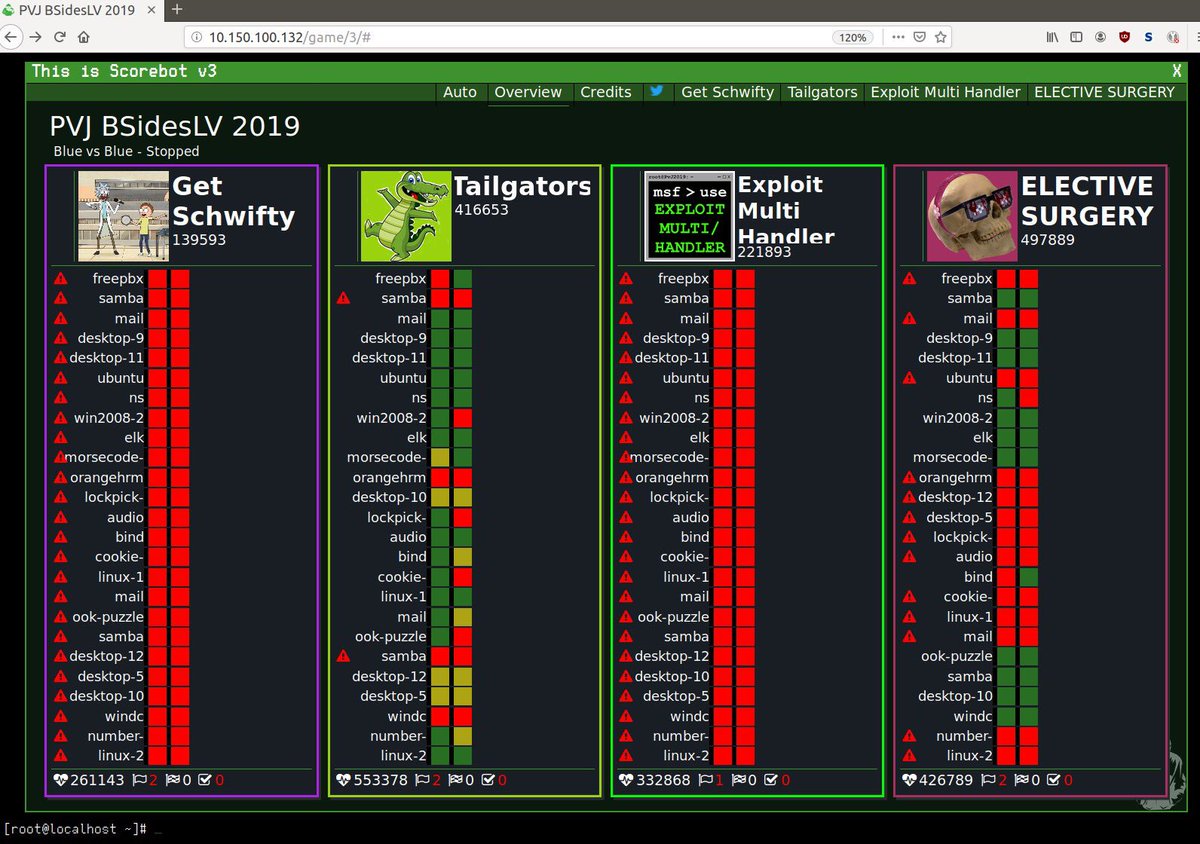
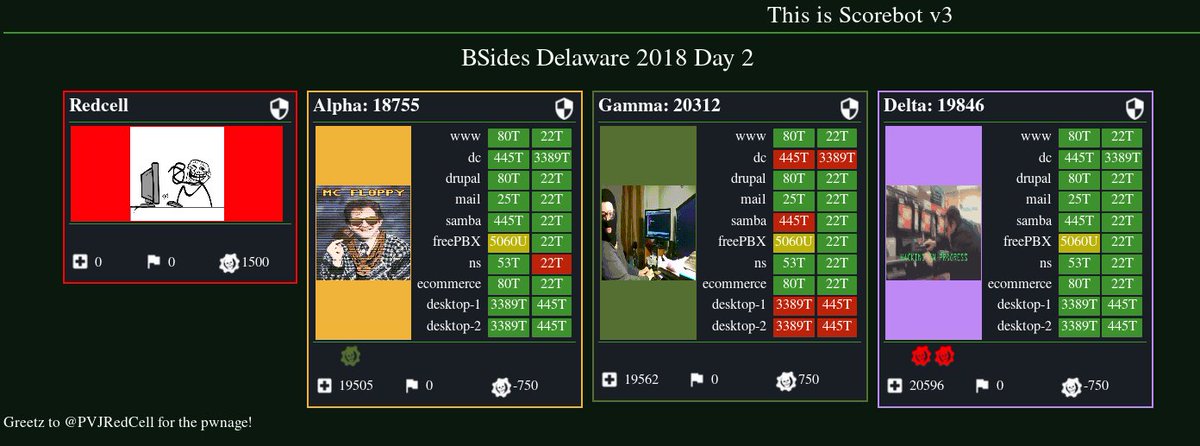

| Team Name |
HingleMcCringleberry |
MeeseeksAndDestroy |
PopPopRet |
RaidersOfTheLostArp |
| Team Score |
652282 |
778136 |
615063 |
874927 |
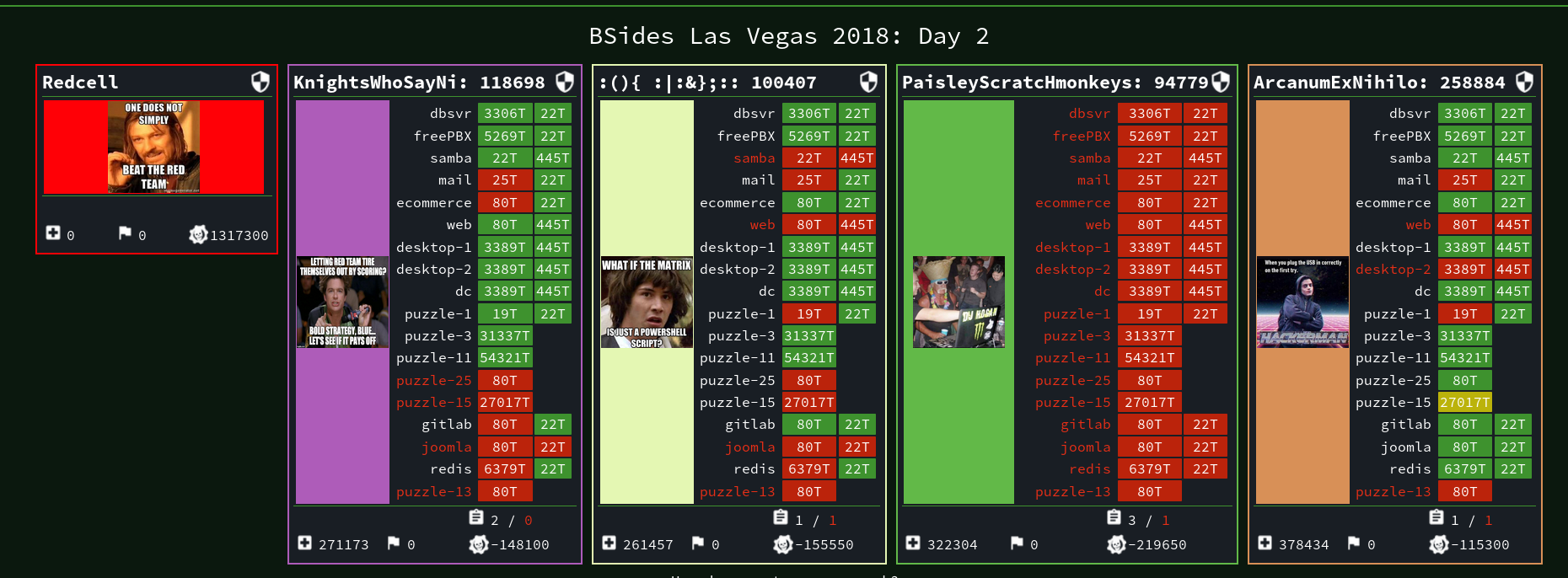
| Team Name |
KnightsWhoSayNi |
:(){ :|:&};:: |
PaisleyScratcHMonkeys |
ArcanumExNihilo |
| Team Score |
118698 |
100407 |
94779 |
258884 |
Thanks to Wilmington University for hosting the CTF

Thanks to Maven Security for supporting the CTF

Thanks to Palo Alto Networks for donating NGFW VMs and the support of one of their subject matter experts

Thanks to Wilmington University for hosting the CTF

Thanks to Maven Security for supporting the CTF

Thanks to Palo Alto Networks for donating NGFW VMs and the support of one of their subject matter experts

Final Scores
Thanks to Wilmington University for hosting the CTF

Thanks to Maven Security for supporting the CTF

Thanks to Palo Alto Networks for donating NGFW VMs and the support of one of their subject matter experts

Thanks to Strategic Cyber LLC for supporting the CTF

Thanks to SecureWorks for their Red Team support


Thanks to Wilmington University for hosting the CTF

Thanks to Maven Security for supporting the CTF

| team name |
Infinite Improbability |
The SYNdicate |
Team Machine |
JMP-ESP |
| Day 1 total |
17,860 |
20,788 |
20,943 |
19,886 |
| Day 2 total |
3,114 |
20,148 |
-299,571 |
-24,335 |
| Grand Total |
20,974 |
40,936 |
-278,628 |
-4,449 |
We’d like to thank RSA for the donation of their appliance, without which the PCAPs from the 2016 Pros V Joes CTF would not be available.
Many thanks ot Maven Security for the donation of many hours of their employee's time to help prepare and run the 2016 BSLV Pros V Joes CTF. Without that contribution, the game would not have been nearly as successful!

Above all, we'd like to thank Wilmington University for the continued use of their facilities to host our CTF.

This year, we had the misfortune to deal with a critical bug in Scorebot, the program that we use to run the ProsVJoes CTF. This bug seriously impacted the scores displayed on the game board, which was inaccurately representing the state of the game for both days.
Right up front, I would like to personally apologize to all of our players for this flaw, and for the ill feelings this may have caused. I have never seen a Pros V Joes CTF where so many people put in so much effort for so long before the actual game. It is only natural that these fine people have an emotional investment in the game, and so may have been extremely disappointed in the final results once they were published on Twitter.
Unfortunately, the bug is what is, and I can only do the best I can to make it right and fair after the fact, now that this year’s game has concluded.
As a small mercy, the bug was isolated in scope to only the ticket scoring portion of the game. The rules state that players must close tickets as a part of the game. To score them on this, the scoring software monitors the open and closed tickets. The design had been that the open tickets a Blue Team had would cost them 50 points per service scoring round (about 3 minutes, on average).
Here’s where the bug comes in.
Scorebot was docking each team 50 points per service round for every closed ticket.
The bug was discovered on day two by one of our volunteers this year, Gambite, so a big shout out to him.
Unfortunately, no way exists to handle this bug during run time. Once Scorebot starts, that’s it, she’s off and running for the duration. So our only choice was to fix things after game play stopped.
For the second day, we had the entire ticket database - every flag, when each was opened, and when each was closed. So, we could go back and calculate what the final ticket score was for day two.
For the first day, we had no such advantage. Historically, we wipe the ticket database at the start of day two, so that the prior day’s tickets are no longer counted, since each day’s game play is independent. While scorebot generates a great deal of log data to track almost every event in the game, the ticket code does not currently log open / closed tickets for every scoring round. That’s bug number two. This was a simple, yet damaging oversight in the code base that will be corrected before the next game.
So, in the end, we were able to recalculate the correct scoring for day two, but we did not have the data needed to do the same for day one.
So what did the numbers look like for day two? Here’s what they were, and what they changed to:
| team name |
Infinite |
SYNdicate |
Team Machine |
JMP-ESP |
| Old Tickets |
-198,000 |
-156,350 |
-63,650 |
-297,350 |
| New Tickets |
-4,250 |
-14,900 |
-314,750 |
-14,000 |
As can be seen, this is a drastic change. Again, it is a consequence of the bug counting closed tickets as open when calculating the amount of points to take away each service round.
As a result, here’s what day two looks like after taking these new scores into account:
| team name |
Infinite |
SYNdicate |
Team Machine |
JMP-ESP |
| services |
20,464 |
20,648 |
19,779 |
20,165 |
| flags |
600 |
15,400 |
7,600 |
-3,500 |
| tickets |
-198,000 |
-156,350 |
-63,650 |
-297,350 |
| beacons |
-13,700 |
-1,000 |
-12,200 |
-27,000 |
| Old Total |
-190,636 |
-121,302 |
-48,471 |
-307,685 |
|
|
|
|
|
|
| New Tickets |
-4250 |
-14,900 |
-314,750 |
-14,000 |
| New Ticket Total |
3114 |
20,148 |
-299,571 |
-24,335 |
For day one, we did not have the data needed to make that sort of a recalculation. As a result, our only options were to count the data as is, or discard that part of the score entirely.
We chose to discard the tickets, which seemed the most fair to the teams that had been diligent in closing their tickets. Here is what day one looks like, with that choice:
| team name |
Infinite |
SYNdicate |
Team Machine |
JMP-ESP |
| services |
21,360 |
20,588 |
19,943 |
20,086 |
| flags |
400 |
1,400 |
2,100 |
2,600 |
| tickets |
-94,800 |
-100,950 |
-64,950 |
-104,750 |
| beacons |
-3,900 |
-1,200 |
-1,100 |
-2,800 |
| total |
-76,940 |
-80,162 |
-44,007 |
-84,864 |
| total w/o tickets |
17,860 |
20,788 |
20,943 |
19,886 |
So, adding up the adjusted first and second day scores as described above, we come up with the results that were published on Twitter:
| team name |
Infinite |
SYNdicate |
Team Machine |
JMP-ESP |
| Day 1 total |
17,860 |
20,788 |
20,943 |
19,886 |
| Day 2 total |
3,114 |
20,148 |
-299,571 |
-24,335 |
| Grand Total |
20,974 |
40,936 |
-278,628 |
-4,449 |
I have personally had multiple conversations with various Blue Pros and Blue Joes from multiple teams on this topic. Thus far, everyone I have explained the circumstances to was understanding about the difficult choices that had to be made. Indeed, three members from Team Machine, undeniably the group that was most impacted by this issue, have agreed to come on staff in spite of this snafu.
Regrettably, my team and I can do nothing about this issue beyond what the solution just described. What we can do, however, is work hard to ensure our future games in the remainder of this year and into next do not suffer from this, nor from any other such egregious flaw. To that end, we’re re-doubling our efforts to clean up the existing 2.x code train, while also restarting effort on the new 3.0 architecture. We will be doing more code reviews and testing, working hard to do our best to prevent a recurrence. Of course, mistakes will happen, but we intend to learn and improve from this one.
To that end, I am pleased to announce that Gambite, the volunteer who found the bug and helped me calculate the correct scores, has signed on to our permanent staff as part of the Pros V Joes dev team.